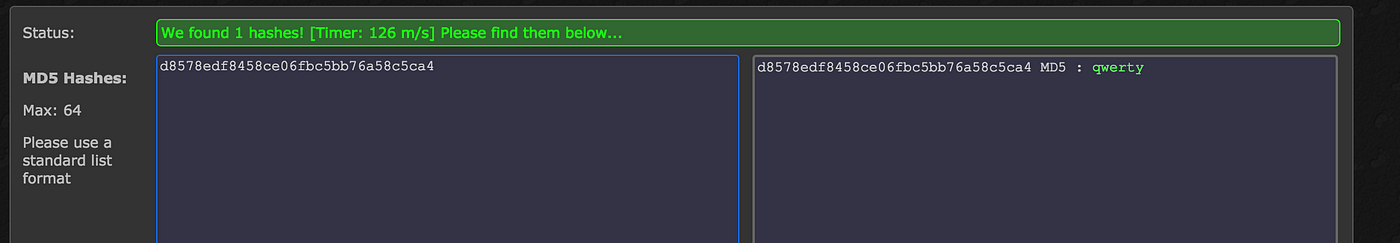
Killer immunoglobulin-like receptors and HLA act both independently and synergistically to modify HIV disease progression | Genes & Immunity

BleepingComputer on Twitter: "Once a threat actor gains access to the NTLM hash, it's as simple as running it through Hashcat to dehash the password. Now the threat actor has both the

Accused killer pit two in fight before choking, torturing WL woman found near Kentland, court doc says
GitHub - shauryasharma-05/PortableKanBan-Hash-Killer: PortableKanBan stores credentials in an encrypted format.






:max_bytes(150000):strip_icc()/latke-breakfast-hash-FT-RECIPE1220-3bd7d7c1768d4d9eb16999f522bbc2ea.jpg)
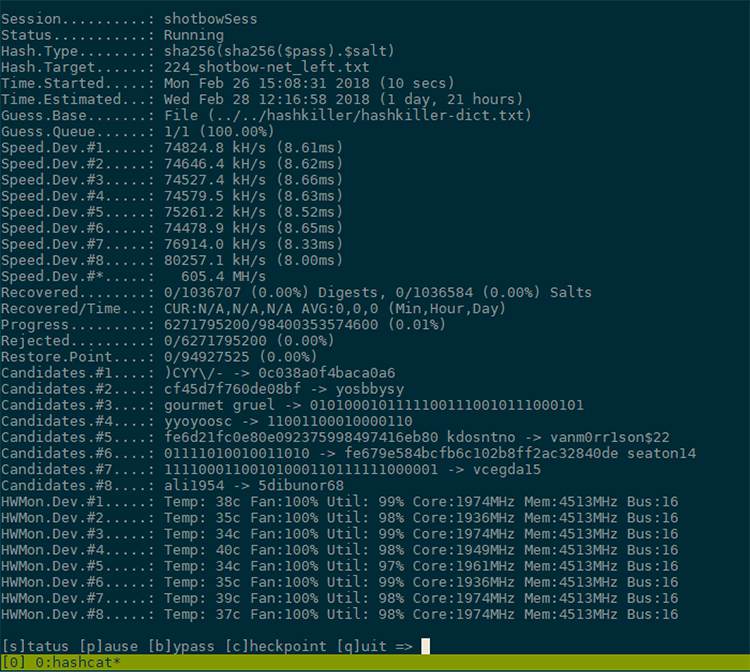


![Hashkiller - Kali Linux - An Ethical Hacker's Cookbook [Book] Hashkiller - Kali Linux - An Ethical Hacker's Cookbook [Book]](https://www.oreilly.com/api/v2/epubs/9781787121829/files/assets/714fa5ac-a3a0-4378-b325-97dee1e71141.png)